I will start by saying that the title is a bit misleading. Security starts at the lowest level (i.e. the server). If you need to use a WordPress plugin to make your website secure, then you need someone to look after your website.
Let’s start with a bird’s eye view on securing your WordPress website:
- Install a server security module (you might need to either contact your host or change hosting completely)
- Harden your server + WordPress configuration (most server hosting panels allow for various settings — see below)
- Use a CDN (i.e. Cloudflare)
- Install a WordPress plugin ← this is what we will discuss below
Server + WordPress configuration may include the below (remember, some of these changes can be done in WordPress):
- Restrict access to files and directories
- Configure security keys
- Block access to
xmlrpc.php - Block directory browsing
- Forbid execution of PHP scripts in the
wp-includesdirectory - Forbid execution of PHP scripts in the
wp-content/uploadsdirectory - Block access to
wp-config.php - Disable scripts concatenation for WordPress admin panel
- Turn off pingbacks
- Disable unused scripting languages
- Disable PHP execution in cache directories
- Disable file editing in WordPress Dashboard
- Change default database table prefix
- Enable bot protection
- Block access to sensitive files
- Block access to potentially sensitive files
- Block access to
.htaccessand.htpasswd - Block author scans
- Change default administrator’s username
Let’s talk about option number 4 — using a WordPress plugin. I had the opportunity to work on 2 hosting servers during a malware attack that lasted for months. This gave me the “ammunition” to test my plugin, use trial and error techniques, and constantly update and improve the malware detection code.
One of the servers was under a malware attack, while the other one had around 50-60 spam registrations per day. Before I started working on it, the spam registrations reached 30,000+ users.
Malware Attacks
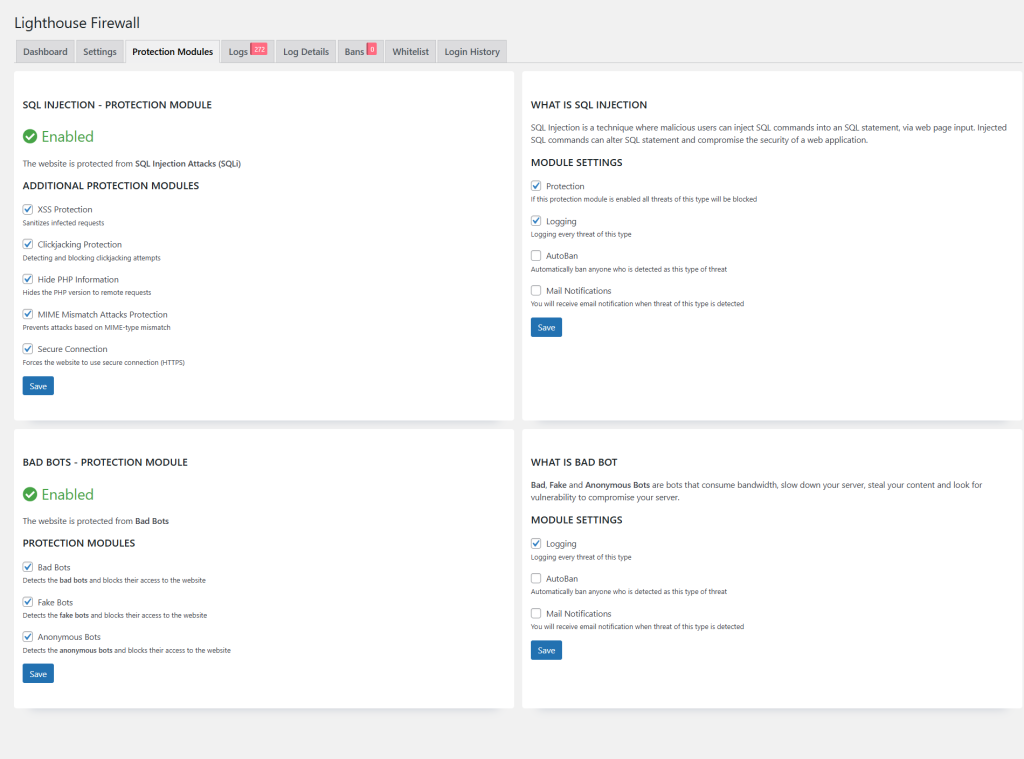
Going back to my initial list, number 2 can be achieved by setting rules in the Apache/Nginx configuration files. Lighthouse does the same, but using PHP. While not ideal, it will stop 90% of the attacks.
Lighthouse will block various URL patterns known to trigger SQL injection or remote code execution. It will also block artificial users, or bots. Lighthouse will try to match the visitor’s behaviour with a real user (i.e. no arbitrary POST requests, no empty headers, no fake user agents, and more).
As a quick note, even if your server is 100% configured at all levels, if a serious hacker want to hack you, they will.
Spam Registrations
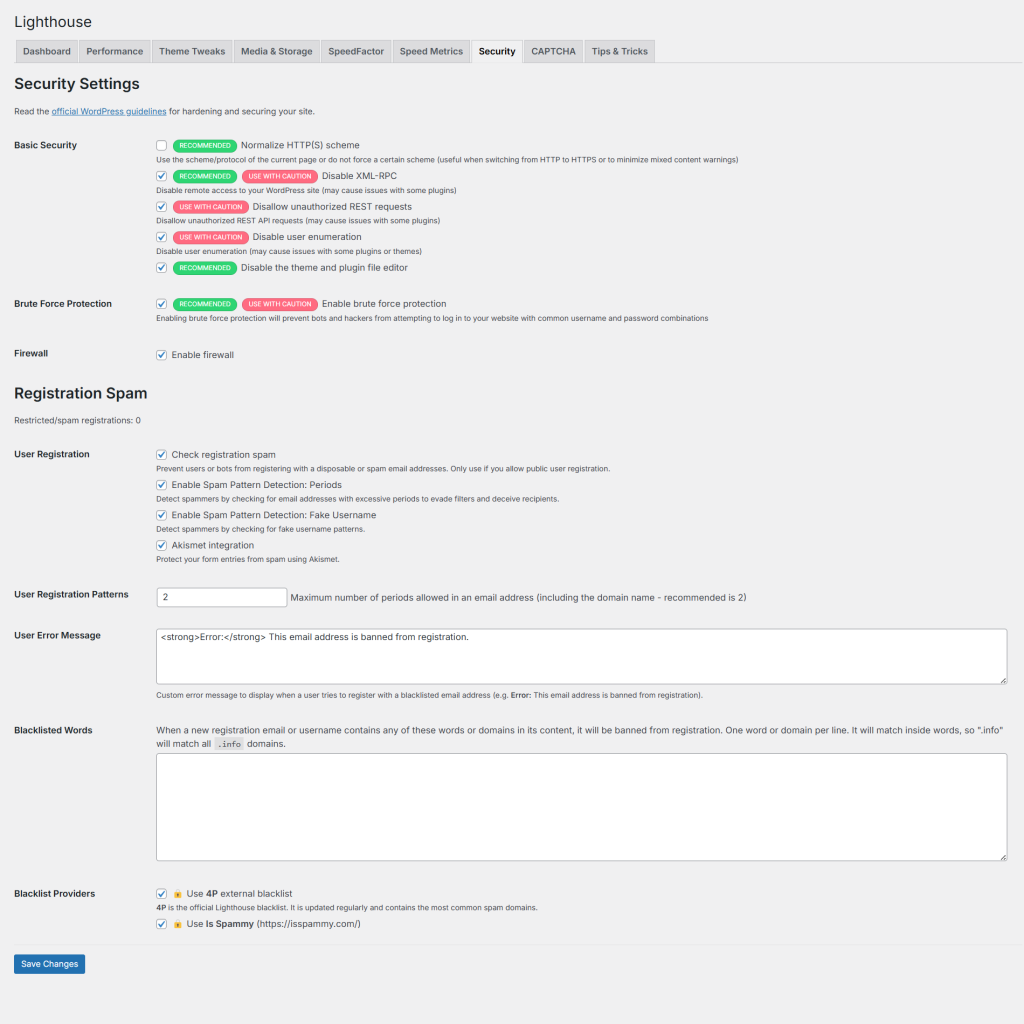
Having full access to the affected hosting server, I built a custom blacklist (currently maintained on GitHub), an Akismet API, an IsSpammy API and various username or email address patterns, common to spammers. The actions above virtually stopped most spam registrations. The rest of them were blocked by implementing a custom login form (as most automated registrations will look for wp-login.php).
Recommended Settings
See below the recommended settings for both type of attacks above.